Laboratory of Data Recovery and Analysis
The Data Recovery and Analysis Laboratory was established for specialized training and research in the context of increasing data loss and damage from storage devices.
The Data Recovery and Analysis Laboratory was established for specialized training and research in the context of increasing data loss and damage from storage devices.
The main objective of the research and experiment laboratory is to train students in the principles of secure data storage and to enhance their competence and practical skills in recovering lost electronic data. Experts and scientists use laboratory techniques to develop new methods and solutions in the reconstruction and decryption of encrypted and stored data.
Thanks to the integration of high technology in data recovery and leading experts, the research and experiment lab not only trains students but also provides services for businesses in analysis, recovery, decrypted and deleted or seemingly unrecoverable data.
The data recovery and analysis lab is the only one that can serve the whole enterprise
The University of Rzeszów forms a data analysis and recovery laboratory with the same orientation as the response, rescue, analytical processing, and data recovery centers. The standard of setting up a data analysis and recovery lab is similar to that of a police and security unit, which can fulfill the requirements of court, police, or defense service. Currently, in Poland, this is the data recovery research, and an experimental laboratory of the university can perform this task.
Serving scientists
The lab can be used by scientists to study computer forensics such as computer analysis, mobile device analysis, and network analysis. The lab also allows data recovery from electronic media and mobile devices.
The Research and Data Recovery Laboratory also helps scientists, Master’s and PhD students in:
-Analytics based on data flow,
-Detecting steganographic content,
-Build and recover compressed data,
-Display data for forensics.
-Decoding and testing electronic data security algorithms,
-Analyzing hardware support for mathematical operations using CUDA technology,
-Developing algorithms to reconstruct data, metadata, and files,
-Analyzing and using software for electronic data collection and algorithms for recovery.
Serving students:
UITM students are equipped with specialized equipment and software, including EnCase Forensic, the world’s most important and expensive program in computer forensics. This software is used by investigative, military and intelligence units. EnCase Forensic allows students to quickly search, analyze, and save evidence electronically.
Serving business
-Electronic data recovery from functionally and mechanically damaged data suppliers, such as hard drives, disk drives and flash memory cards, CDs, DVDs, Blu-Rays.
-Recovering data from mobile devices: phones, smartphones, SIM cards, tablets, GPS navigation and more.
-Recovering passwords and contents of encrypted files, such as Microsoft Office, Corel WordPerfect Office, Lotus formatted documents, PDF files, ZIP compressed archives, RAR files and many more.
-Permanently and irrecoverably deleting confidential data while maintaining the storage efficiency of the devices.
Equipment
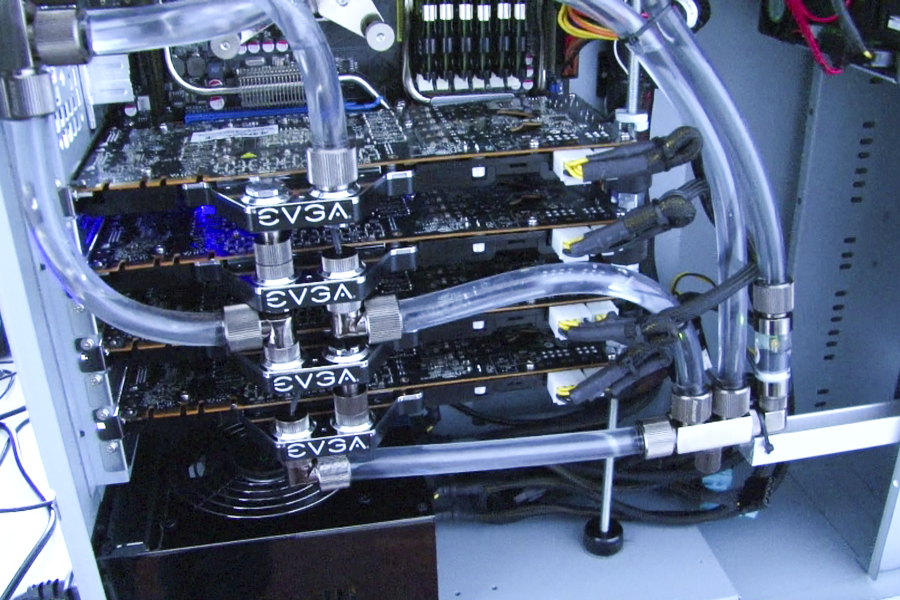
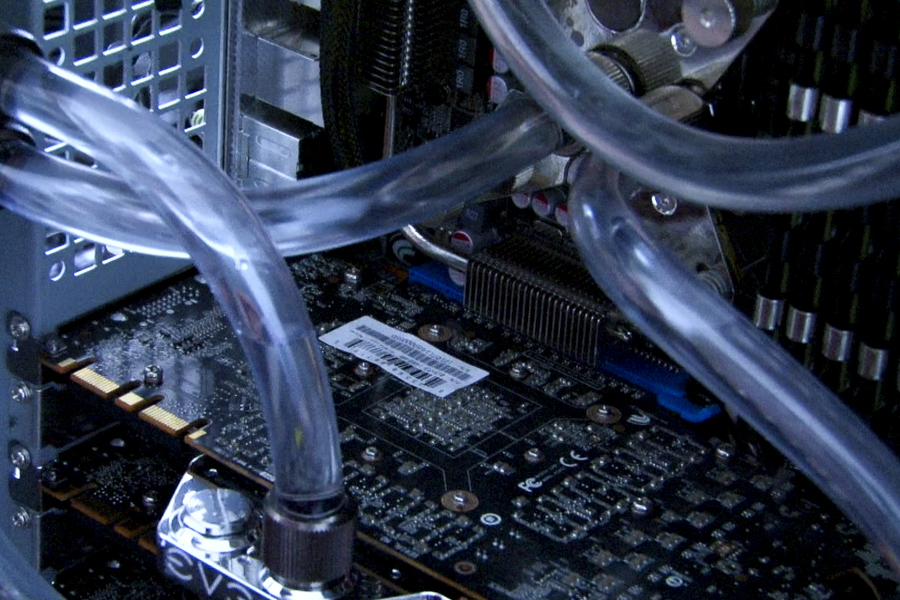
-Supercomputers: FRED, FRED DX, FRED SC are used for complex long-term and computational data analysis processes, as well as laptop forensics suites.
-Super Kit tablet, prevents data changes on disk and loads new information.
-XRY system – the best system for investigative analysis of mobile devices: phones, PDAs, navigation, etc. This system helps get a list of connections, photos, SMS messages, videos, etc.
-Specialized software and the right connectivity allow you to connect more than 4 thousand different devices (phones, smartphones, SIM cards, GPS, etc.).
-Computer system.